GuardDuty is a very solid service but it can give you some challenges when you have several AWS accounts spanning several regions. So here’s a way to manage all the findings from several accounts and regions. This how-to summarizes the steps and will provide links to already published ones from AWS.
1) — Pick a Master Account where you can manage/view all the findings for all your accounts. This is a quick how-to: https://aws.amazon.com/blogs/security/how-to-manage-amazon-guardduty-security-findings-across-multiple-accounts/
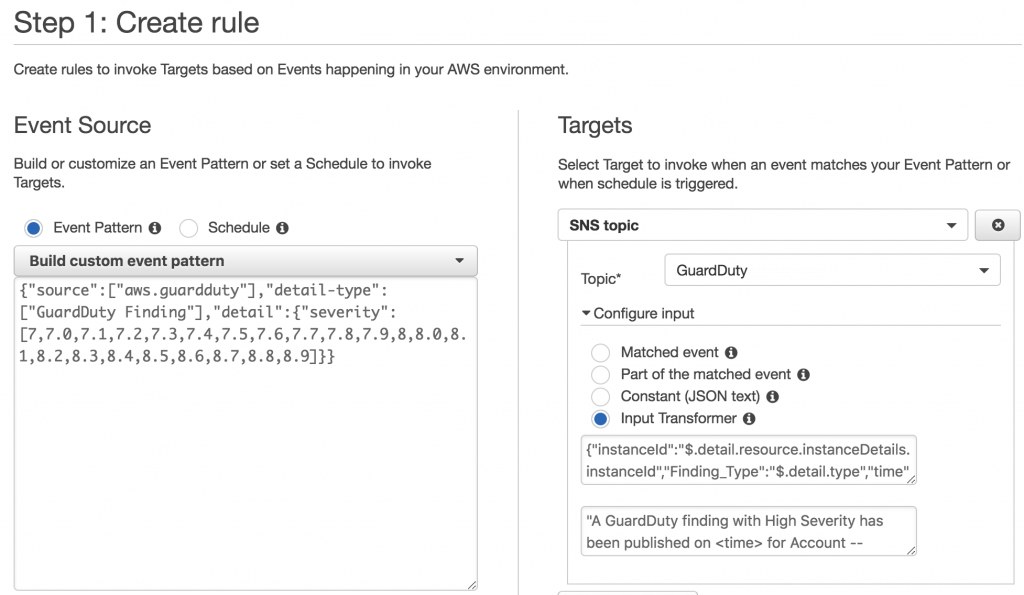
2) — In the Master account, create a CloudWatch Rule that will send a notification to an email address for high severity findings. Your cloudwatch rule will have an event pattern for high severity findings which will look like this:
{“source”:[“aws.guardduty”],”detail-type”:[“GuardDuty Finding”],”detail”:{“severity”:[7,7.0,7.1,7.2,7.3,7.4,7.5,7.6,7.7,7.8,7.9,8,8.0,8.1,8.2,8.3,8.4,8.5,8.6,8.7,8.8,8.9]}}
Here is how you can create a CloudWatch Rule. https://docs.aws.amazon.com/AmazonCloudWatch/latest/events/Create-CloudWatch-Events-Rule.html
3) — The cloudwatch rule will have an SNS topic for its target. Create an SNS topic and subscribe to the topic (via email):
https://docs.aws.amazon.com/sns/latest/dg/sns-getting-started.html#CreateTopic
4) — In this how-to, the emails go to a Teams channel email address which is monitored by Ops folks. The email message (by default) will be long and fairly difficult to read. To shorten the message and include only the relevant information, in the cloudwatch rule target, use Input Transformer and use these for your Input Path and Input Template:
Input Path: {“instanceId”:”$.detail.resource.instanceDetails.instanceId”,”Finding_Type”:”$.detail.type”,”time”:”$.time”,”region”:”$.region”,”account”:”$.account”}
Input Template:
“A GuardDuty finding with High Severity has been published on for Account — — in — — for with these details ==> “
5) — Repeat steps (from the Master account) for other regions.
